Crypto: The amazing secret of Cryptography, Cryptocurrencies and Blockchain
History
We use cryptography every day—often without even realising it. In today’s world, cryptography plays a key role in far more than just securing communications. It protects mobile phone calls, paid digital television, Wi-Fi networks, public transport ticketing systems, banking transactions, and even helps to filter out spam in emails. But let’s take a step back and explore the history of this fascinating science, one that has always been wrapped in secrecy, and which has become one of the hottest topics of recent years.

From Ancient Codes to Mathematical Ciphers
The history of cryptography dates back nearly 4,000 years. One of the earliest known uses comes from Ancient Egypt, where special hieroglyphs were used to conceal the meaning of messages. Cryptographic methods also appear in Jewish religious texts, including the Book of Jeremiah from the 6th century BC, where a simple substitution cypher known as Atbash was used. Another early example is the scytale, a device attributed to ancient Sparta and used to encode military messages.
The term comes from the Greek words kryptos (hidden) and graphē (writing). Over time, cryptography developed as a science aimed at securing information through secrecy, ensuring data integrity (preventing undetected tampering), verifying authenticity (confirming the source or authorship), and providing non-repudiation (making it impossible to deny sending a message).
Early cryptography focused mainly on encryption, the reversible transformation of readable (plaintext) information into unreadable (ciphertext) using a secret key or algorithm. In some cases, entire alphabets were substituted with others (e.g., Cyrillic with Greek), and without a key to decode them, the message remained unreadable.
From the early to mid-20th century, cryptography advanced significantly with the help of electromechanical devices. During World War II, it became deeply mathematical, involving renowned mathematicians such as Claude Shannon (USA), Alan Turing (UK), Hans Rohrbach (Germany), and Alexander Osipovich Gelfond (USSR). With the rise of computers, cryptography evolved into a distinct scientific field at the intersection of mathematics and computer science. Today, research in cryptography is published in academic journals and presented at international conferences.
The Rise of Public-Key
The modern era began in the late 1970s with the invention of public-key . Unlike classical encryption systems, which require both sender and receiver to share a secret key, public-key systems use a pair of mathematically linked keys—one public, one private. This innovation made secure online communication, digital signatures, and e-commerce possible.
Today, cryptography is a cornerstone of many industries, including electronic commerce, digital document management, secure telecommunications, and decentralised finance. It ensures secure identity verification through digital signatures, protects personal data, and underpins most forms of online interaction.
Blockchain Revolution
One of the most transformative applications of cryptography in recent decades is blockchain technology. A blockchain is a growing list of records, or “blocks,” each containing a hash of the previous block, a timestamp, and transaction data. This structure ensures immutability—once information is added to the chain, it cannot be altered without invalidating the entire sequence.
The first blockchain was conceptualised in 2008 by the pseudonymous figure Satoshi Nakamoto, and implemented in 2009 as the foundation of Bitcoin, the world’s first cryptocurrency. In this system, blockchain serves as a public ledger, recording all transactions on the network.

Cryptocurrencies: A New Era of Digital Assets
Bitcoin remains the most well-known and valuable cryptocurrency. Since its launch, thousands of alternative cryptocurrencies—or altcoins—have emerged. Some, like Litecoin, Peercoin, and Namecoin, are direct forks of Bitcoin’s code. Others, like Ethereum, Cardano, and EOS, are entirely new platforms designed to support smart contracts and decentralised applications (dApps).
A third category of digital asset is known as a token. Unlike tokens do not have their own blockchain. Instead, they operate on existing blockchain networks like Ethereum and are commonly used within dApps and DeFi systems.
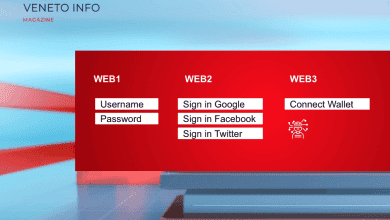
Using and Storing
To use Bitcoin, you first acquire some via an online exchange. Then, you set up a digital wallet—a secure software or hardware device that stores your keys. You can use Bitcoin to pay merchants or individuals, hold it as an investment, or trade it for other cryptocurrencies.
For maximum security, many users rely on hardware wallets such as the Ledger Nano X—a certified device designed to protect private keys from online threats.
Cryptography has grown from ancient secret scripts to one of the most powerful tools in our digital world. It enables secure communication, protects sensitive data, and drives technological revolutions like blockchain and cryptocurrencies. As our dependence on digital systems grows, so too does the importance of this invisible guardian of information.